Stunning Info About Does P2P Leak IP

What Is A P2P Network? YouTube
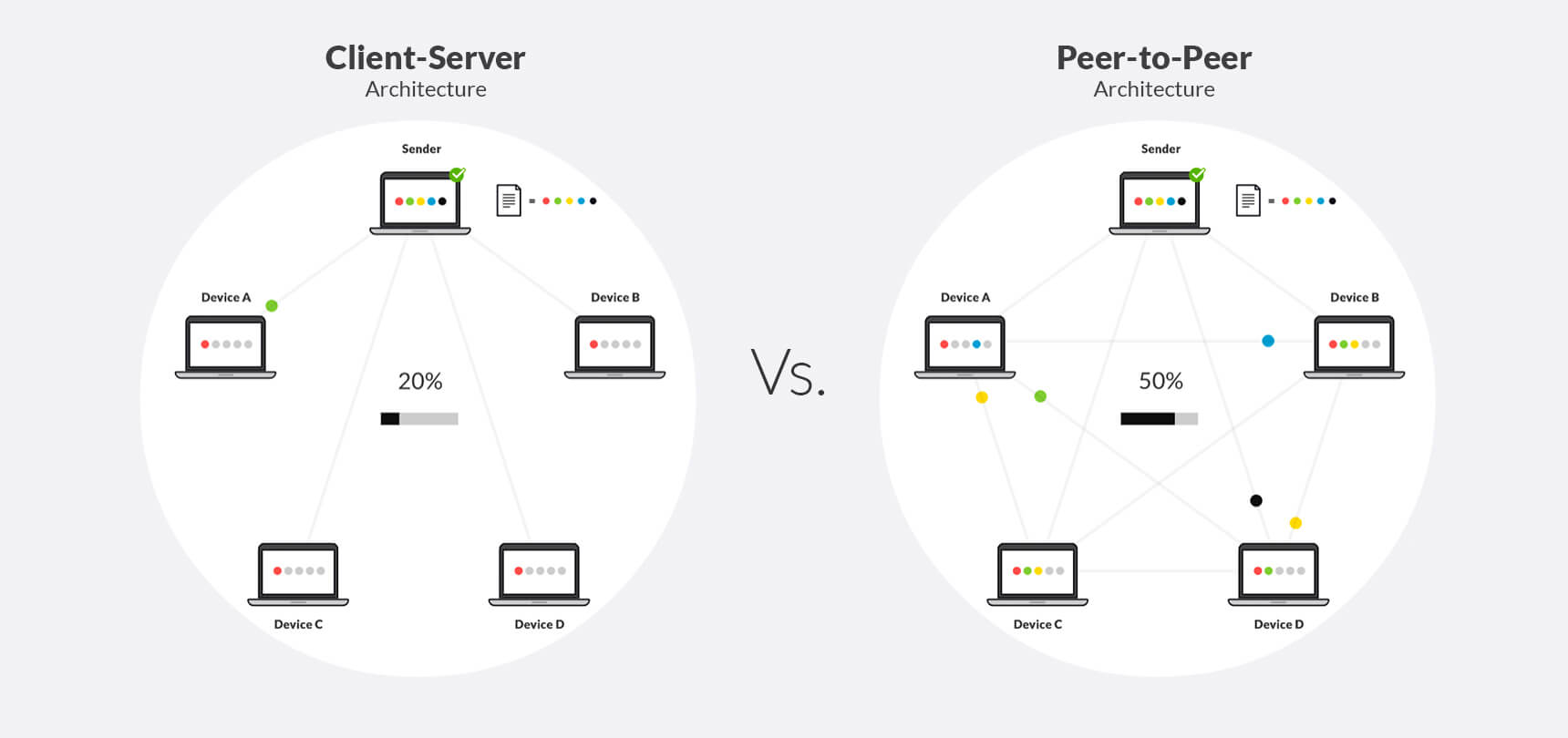
P2P and Your IP Address
1. Understanding the Basics of P2P and IP Addresses
Ever shared a file using a program like BitTorrent? That's Peer-to-Peer (P2P) file sharing in action! It's a way to grab that awesome indie film or that essential software update directly from other users, cutting out the middleman (and potentially saving some bandwidth costs). But here's the thing — while it's super convenient, it also opens a potential window for exposing your IP address.
Think of your IP address as your online home address. It's how websites, servers, and, yes, other P2P users, know where to send data back to you. When you're actively sharing or downloading files on a P2P network, your IP address becomes visible to everyone else participating in that swarm. Not ideal, right?
So, the short answer is: yes, using P2P can potentially expose your IP address. But before you panic and unplug your router, let's dive deeper into why this matters and what you can do about it. The whole "P2P leak IP" concern is valid, but it's manageable. It's like knowing you could get a sunburn at the beach; you take precautions!
It's not just about someone knowing where your internet connection is, it's about what they could potentially do with that information. Your IP can be used to approximate your location, identify your internet service provider (ISP), and, in some cases, be combined with other data to potentially reveal more personal information. So, knowing the risks is the first step in protecting yourself.

Why Your IP Address Matters in the P2P World
2. The Potential Dangers of IP Exposure
Okay, so someone sees your IP address while you're downloading that open-source Linux distribution (purely for ethical reasons, of course!). What's the big deal? Well, depending on the situation, a few not-so-fun things could happen. One potential risk is being targeted by copyright trolls. These are entities that monitor P2P networks for copyrighted material being shared illegally. If they catch your IP address in a swarm, they might send a threatening letter to your ISP, potentially leading to legal action against you.
Beyond copyright issues, there's also the risk of denial-of-service (DoS) attacks. Someone could flood your IP address with traffic, effectively knocking your internet connection offline. This is more likely if you become a prominent figure in a P2P network (e.g., sharing a very popular file). While rare, it's a possibility to consider. It's kinda like leaving your front door unlocked; most of the time nothing happens, but the potential is there.
Let's also think about privacy. While an IP address alone doesn't reveal everything about you, it can be used to build a profile of your online activity. Ad networks, data brokers, and even malicious actors can track your browsing habits, downloads, and other online behavior associated with your IP. It's like having someone quietly observing your every move online.
In some countries, simply having your IP address logged in connection with certain activities (even if those activities aren't technically illegal) can lead to government surveillance. So, while the risk of something serious happening is often low, it's still worth taking steps to protect your IP address, especially when using P2P networks. It's better to be safe than sorry, right?

Link Previews How LINE Leaks IP Addresses Of Users And Bypasses Endto
Shield Up! Protecting Your IP While P2P-ing
3. Practical Steps to Mask Your IP Address
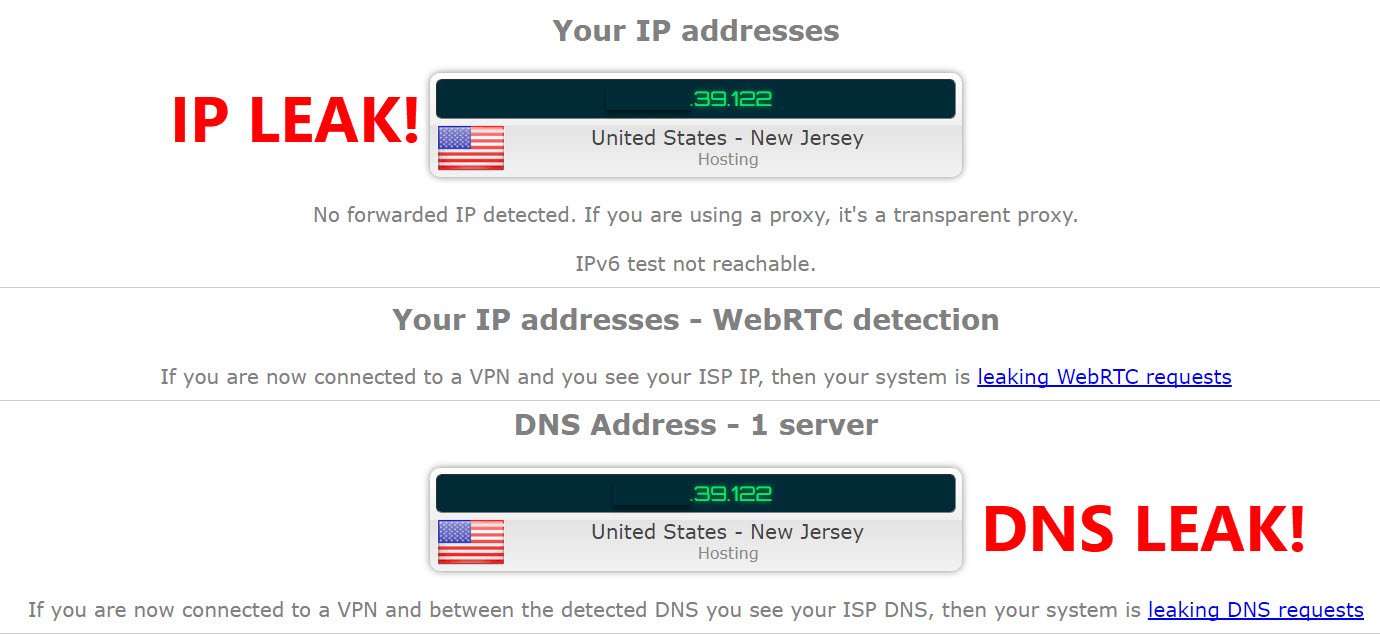
Alright, enough doom and gloom! Let's talk about how you can enjoy the benefits of P2P without broadcasting your IP address to the world. One of the most popular and effective methods is using a Virtual Private Network (VPN). A VPN encrypts your internet traffic and routes it through a server in a location of your choice, effectively masking your real IP address with the VPN server's IP. This means that instead of your IP being visible in the P2P swarm, the VPN's IP is displayed.
Another option is using a proxy server. Similar to a VPN, a proxy server acts as an intermediary between your computer and the internet. However, proxies typically offer less encryption than VPNs, so they might not be as secure. Still, they can provide a basic level of IP masking. Think of it as wearing a simple disguise instead of full-blown incognito mode.
Certain P2P clients also have built-in features for anonymity, such as encryption and IP filtering. Make sure to enable these features in your P2P client's settings. Read the documentation and explore the options to see what kind of privacy controls are available. It's like locking the windows and doors of your house; it adds an extra layer of security.
Finally, consider using a seedbox. A seedbox is a dedicated server that is used for uploading and downloading files from P2P networks. Because the seedbox is located in a data center with a high-speed internet connection, it can download and upload files much faster than your home computer. And, more importantly, it hides your IP address from other users on the P2P network. It's like having a professional moving company handle all your stuff, ensuring everything is done safely and discreetly.
Choosing the Right VPN for P2P
4. VPN Features to Look For
Not all VPNs are created equal, especially when it comes to P2P file sharing. Some VPNs explicitly prohibit P2P traffic on their servers, while others actively support it. So, before you sign up for a VPN, make sure it allows P2P on its servers. Check their terms of service or contact their customer support to confirm. Imagine signing up for a gym only to find out you can't lift weights! That's kind of the same thing.
Another important factor is the VPN's logging policy. A good VPN should have a strict no-logs policy, meaning it doesn't track or store any of your online activity, including your IP address, browsing history, and connection timestamps. Look for VPNs that have been independently audited to verify their no-logs claims. It's like trusting a doctor with your health; you want to make sure they're reputable and trustworthy.
Speed is also crucial. P2P file sharing can be bandwidth-intensive, so you need a VPN that offers fast and reliable connection speeds. Test the VPN's speed using a speed test tool before committing to a long-term subscription. Nothing's worse than a VPN that slows your download speeds to a crawl.
Finally, consider the VPN's server locations. The more server locations a VPN has, the more options you have for masking your IP address and bypassing geographical restrictions. Choose a VPN with servers in countries that have strong privacy laws. It's like having multiple escape routes; the more options, the better.
Beyond VPNs
5. Staying Safe in the P2P Ecosystem
While a VPN is a great tool, it's not the only way to stay safe while using P2P. It's crucial to download files from reputable sources. Check the comments and ratings on torrent websites before downloading anything. Avoid downloading files from unknown or suspicious sources, as they might contain malware or viruses. It's like eating street food; you want to make sure it's from a clean and trustworthy vendor.
Always run a virus scan on downloaded files before opening them. Use a reputable antivirus program and keep it up to date. Even if you trust the source of the file, it's always a good idea to scan it for malware. Think of it as washing your hands before eating; it's a simple precaution that can prevent illness.
Keep your P2P client software up to date. Software updates often include security patches that fix vulnerabilities that could be exploited by malicious actors. Enable automatic updates in your P2P client settings to ensure you're always running the latest version. It's like keeping your car in good repair; regular maintenance can prevent breakdowns.
Be mindful of what you share. Avoid sharing sensitive information, such as your personal documents, financial records, or passwords, on P2P networks. It's like leaving your wallet unattended in a public place; it's just asking for trouble. By taking these precautions, you can significantly reduce the risk of exposing your IP address and other personal information while using P2P networks. It's about being smart, cautious, and proactive in protecting your online privacy.

FAQ
6. Your P2P Questions Answered
Q: Will I automatically get a fine if my IP is seen in a P2P swarm?
A: Not necessarily. It depends on what you were sharing (if anything illegal) and the laws in your country. Copyright trolls often send out mass letters, but not everyone who gets one actually faces legal action.Q: Can my ISP see what I'm downloading even with a VPN?
A: A good VPN encrypts your traffic, preventing your ISP from seeing the contents of your downloads. However, they can still see that you're using a VPN.Q: Are all P2P programs risky?
A: Not all P2P programs are inherently risky, but they all have the potential to expose your IP address. It's more about how you use them and what precautions you take.